共计 10835 个字符,预计需要花费 28 分钟才能阅读完成。

最近一大早收到微信告警,大早上的,阿祖就干活了,这么勤奋的吗?
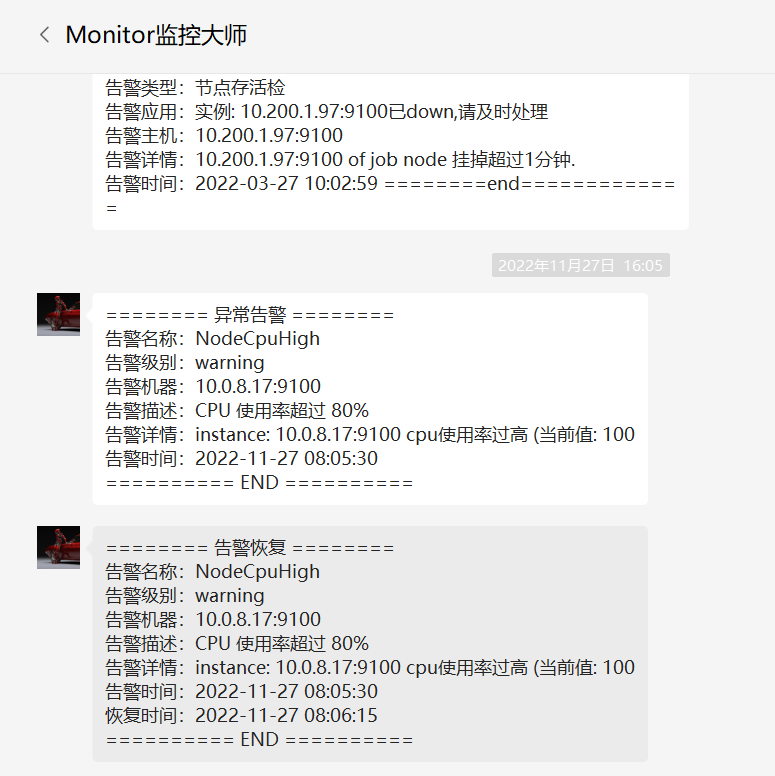
登上服务器查看了下进程都是php-fpm占用高,想到有可能是有人在刷,所以去查看了下访问日志,发现有大量的这种请求:
192.30.89.51 - - [26/Nov/2022:22:22:31 +2700] "POST /xmlrpc.php HTTP/1.1" 405 415 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36"
64.42.179.43 - - [26/Nov/2022:22:31:23 +2700] "POST /xmlrpc.php HTTP/1.1" 405 415 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36"
194.187.251.155 - - [26/Nov/2022:22:42:50 +2700] "POST /xmlrpc.php HTTP/1.1" 405 415 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36"
194.187.251.155 - - [26/Nov/2022:22:43:28 +2700] "POST /xmlrpc.php HTTP/1.1" 405 415 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36"
193.37.254.3 - - [26/Nov/2022:22:59:04 +2700] "POST /xmlrpc.php HTTP/1.1" 405 415 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36"
20.211.26.115 - - [26/Nov/2022:23:13:59 +2700] "GET //xmlrpc.php?rsd HTTP/1.1" 200 816 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36"
20.211.26.115 - - [26/Nov/2022:23:14:06 +2700] "POST //xmlrpc.php HTTP/1.1" 200 413 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36"
184.75.221.211 - - [26/Nov/2022:23:14:48 +2700] "POST /xmlrpc.php HTTP/1.1" 405 415 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36"
199.249.230.17 - - [27/Nov/2022:00:38:52 +2700] "POST /xmlrpc.php HTTP/1.1" 405 415 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36"
213.152.161.219 - - [27/Nov/2022:01:09:39 +2700] "POST /xmlrpc.php HTTP/1.1" 405 415 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36"
134.19.179.187 - - [27/Nov/2022:01:35:52 +2700] "POST /xmlrpc.php HTTP/1.1" 405 415 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36"
91.226.102.163 - - [27/Nov/2022:02:24:52 +2700] "POST /xmlrpc.php HTTP/1.1" 405 415 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36"
46.183.220.203 - - [27/Nov/2022:02:37:40 +2700] "POST /xmlrpc.php HTTP/1.1" 405 415 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36"
199.249.230.37 - - [27/Nov/2022:04:38:10 +2700] "POST /xmlrpc.php HTTP/1.1" 405 415 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36"
184.75.221.180 - - [27/Nov/2022:04:46:10 +2700] "POST /xmlrpc.php HTTP/1.1" 405 415 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36"
82.102.27.195 - - [27/Nov/2022:04:47:49 +2700] "POST /xmlrpc.php HTTP/1.1" 405 415 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36"
46.183.220.203 - - [27/Nov/2022:06:17:56 +2700] "POST /xmlrpc.php HTTP/1.1" 405 415 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36"
146.70.76.35 - - [27/Nov/2022:06:35:24 +2700] "POST /xmlrpc.php HTTP/1.1" 405 415 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36"
.........略
.........略
150.158.146.240 - - [27/Nov/2022:08:06:23 +2700] "GET /xmlrpc.php HTTP/1.1" 405 53 "-" "Mozilla/5.0 (Windows NT 6.1; WOW64; rv:45.0) Gecko/20100101 Firefox/45.0"
150.158.146.240 - - [27/Nov/2022:08:06:25 +2700] "POST /xmlrpc.php HTTP/1.1" 405 415 "http://www.xadocker.cn/xmlrpc.php" "python-requests/2.27.1"
150.158.146.240 - - [27/Nov/2022:08:06:25 +2700] "POST /xmlrpc.php HTTP/1.1" 405 415 "http://www.xadocker.cn/xmlrpc.php" "python-requests/2.27.1"
150.158.146.240 - - [27/Nov/2022:08:06:26 +2700] "POST /xmlrpc.php HTTP/1.1" 405 415 "http://www.xadocker.cn/xmlrpc.php" "python-requests/2.27.1"
150.158.146.240 - - [27/Nov/2022:08:06:26 +2700] "POST /xmlrpc.php HTTP/1.1" 405 415 "http://www.xadocker.cn/xmlrpc.php" "python-requests/2.27.1"
150.158.146.240 - - [27/Nov/2022:08:06:27 +2700] "POST /xmlrpc.php HTTP/1.1" 405 415 "http://www.xadocker.cn/xmlrpc.php" "python-requests/2.27.1"
150.158.146.240 - - [27/Nov/2022:08:06:27 +2700] "POST /xmlrpc.php HTTP/1.1" 405 415 "http://www.xadocker.cn/xmlrpc.php" "python-requests/2.27.1"
150.158.146.240 - - [27/Nov/2022:08:06:27 +2700] "POST /xmlrpc.php HTTP/1.1" 405 415 "http://www.xadocker.cn/xmlrpc.php" "python-requests/2.27.1"
150.158.146.240 - - [27/Nov/2022:08:06:28 +2700] "POST /xmlrpc.php HTTP/1.1" 405 415 "http://www.xadocker.cn/xmlrpc.php" "python-requests/2.27.1"
150.158.146.240 - - [27/Nov/2022:08:06:28 +2700] "POST /xmlrpc.php HTTP/1.1" 405 415 "http://www.xadocker.cn/xmlrpc.php" "python-requests/2.27.1"
150.158.146.240 - - [27/Nov/2022:08:06:29 +2700] "POST /xmlrpc.php HTTP/1.1" 405 415 "http://www.xadocker.cn/xmlrpc.php" "python-requests/2.27.1"
.........略
.........略更改nginx日志,增加请求体打印
log_format main '$remote_addr - $remote_user [$time_local] "$request" '
'"$http_referer" $status $body_bytes_sent $request_body '
'"$http_user_agent" "$http_x_forwarded_for"';再看下日志:
113.119.67.232 - - [27/Nov/2022:08:28:37 +0800] "POST /xmlrpc.php HTTP/1.1" "https://www.xadocker.cn/xmlrpc.php" 405 415 \x0A <?xml version=\x221.0\x22 encoding=\x22iso-8859-1\x22?>\x0A <methodCall>\x0A <methodName>wp.getUsersBlogs</methodName>\x0A <params>\x0A <param><value>xadocker</value></param>\x0A <param><value>z1x2c3v4</value></param>\x0A </params>\x0A </methodCall>\x0A "python-requests/2.27.1" "-"
113.119.67.232 - - [27/Nov/2022:08:28:45 +0800] "POST /xmlrpc.php HTTP/1.1" "https://www.xadocker.cn/xmlrpc.php" 405 415 \x0A <?xml version=\x221.0\x22 encoding=\x22iso-8859-1\x22?>\x0A <methodCall>\x0A <methodName>wp.getUsersBlogs</methodName>\x0A <params>\x0A <param><value>xadocker</value></param>\x0A <param><value>z1a2q3</value></param>\x0A </params>\x0A </methodCall>\x0A "python-requests/2.27.1" "-"
113.119.67.232 - - [27/Nov/2022:08:28:52 +0800] "POST /xmlrpc.php HTTP/1.1" "https://www.xadocker.cn/xmlrpc.php" 405 415 \x0A <?xml version=\x221.0\x22 encoding=\x22iso-8859-1\x22?>\x0A <methodCall>\x0A <methodName>wp.getUsersBlogs</methodName>\x0A <params>\x0A <param><value>xadocker</value></param>\x0A <param><value>golden</value></param>\x0A </params>\x0A </methodCall>\x0A "python-requests/2.27.1" "-"
113.119.67.232 - - [27/Nov/2022:08:28:55 +0800] "POST /xmlrpc.php HTTP/1.1" "https://www.xadocker.cn/xmlrpc.php" 405 415 \x0A <?xml version=\x221.0\x22 encoding=\x22iso-8859-1\x22?>\x0A <methodCall>\x0A <methodName>wp.getUsersBlogs</methodName>\x0A <params>\x0A <param><value>xadocker</value></param>\x0A <param><value>adminsec1234</value></param>\x0A </params>\x0A </methodCall>\x0A "python-requests/2.27.1" "-"
113.119.67.232 - - [27/Nov/2022:08:28:56 +0800] "POST /xmlrpc.php HTTP/1.1" "https://www.xadocker.cn/xmlrpc.php" 405 415 \x0A <?xml version=\x221.0\x22 encoding=\x22iso-8859-1\x22?>\x0A <methodCall>\x0A <methodName>wp.getUsersBlogs</methodName>\x0A <params>\x0A <param><value>xadocker</value></param>\x0A <param><value>1a2s3d4f</value></param>\x0A </params>\x0A </methodCall>\x0A "python-requests/2.27.1" "-"
113.119.67.232 - - [27/Nov/2022:08:28:57 +0800] "POST /xmlrpc.php HTTP/1.1" "https://www.xadocker.cn/xmlrpc.php" 405 415 \x0A <?xml version=\x221.0\x22 encoding=\x22iso-8859-1\x22?>\x0A <methodCall>\x0A <methodName>wp.getUsersBlogs</methodName>\x0A <params>\x0A <param><value>xadocker</value></param>\x0A <param><value>1a2s3d</value></param>\x0A </params>\x0A </methodCall>\x0A "python-requests/2.27.1" "-"
113.119.67.232 - - [27/Nov/2022:08:28:58 +0800] "POST /xmlrpc.php HTTP/1.1" "https://www.xadocker.cn/xmlrpc.php" 405 415 \x0A <?xml version=\x221.0\x22 encoding=\x22iso-8859-1\x22?>\x0A <methodCall>\x0A <methodName>wp.getUsersBlogs</methodName>\x0A <params>\x0A <param><value>xadocker</value></param>\x0A <param><value>1z2x3c</value></param>\x0A </params>\x0A </methodCall>\x0A "python-requests/2.27.1" "-"
113.119.67.232 - - [27/Nov/2022:08:28:58 +0800] "POST /xmlrpc.php HTTP/1.1" "https://www.xadocker.cn/xmlrpc.php" 405 415 \x0A <?xml version=\x221.0\x22 encoding=\x22iso-8859-1\x22?>\x0A <methodCall>\x0A <methodName>wp.getUsersBlogs</methodName>\x0A <params>\x0A <param><value>xadocker</value></param>\x0A <param><value>1z2x3c4v</value></param>\x0A </params>\x0A </methodCall>\x0A "python-requests/2.27.1" "-"
113.119.67.232 - - [27/Nov/2022:08:28:58 +0800] "POST /xmlrpc.php HTTP/1.1" "https://www.xadocker.cn/xmlrpc.php" 405 415 \x0A <?xml version=\x221.0\x22 encoding=\x22iso-8859-1\x22?>\x0A <methodCall>\x0A <methodName>wp.getUsersBlogs</methodName>\x0A <params>\x0A <param><value>xadocker</value></param>\x0A <param><value>1t2y3u5i</value></param>\x0A </params>\x0A </methodCall>\x0A "python-requests/2.27.1" "-"
113.119.67.232 - - [27/Nov/2022:08:28:59 +0800] "POST /xmlrpc.php HTTP/1.1" "https://www.xadocker.cn/xmlrpc.php" 405 415 \x0A <?xml version=\x221.0\x22 encoding=\x22iso-8859-1\x22?>\x0A <methodCall>\x0A <methodName>wp.getUsersBlogs</methodName>\x0A <params>\x0A <param><value>xadocker</value></param>\x0A <param><value>1t2y3u</value></param>\x0A </params>\x0A </methodCall>\x0A "python-requests/2.27.1" "-"
好家伙 (╬▔皿▔)凸。。。搜索了一下哎,说这是WP的xmlrpc攻击,用来bao po 用户密码。。。。
兴趣使然,我也来模拟下请求:
创建一个xml body:
<?xml version="1.0" encoding="iso-8859-1"?>
<methodCall>
<methodName>wp.getUsersBlogs</methodName>
<params>
<param><value>manager</value></param>
<param><value>56Omdfd@4w</value></param>
</params>
</methodCall>模拟请求测试:
import requests
import os
url = 'https://www.xadocker.cn/xmlrpc.php'
with open("body_xml",encoding="utf-8") as fp:
body = fp.read()
# print(body)
r = requests.post(url, data=body.encode("utf-8"))
print(r.text)获得如下相应
/home/xadocker/PycharmProjects/untitled/venv/bin/python /home/xadocker/PycharmProjects/untitled/monixml.py
<?xml version="1.0" encoding="UTF-8"?>
<methodResponse>
<fault>
<value>
<struct>
<member>
<name>faultCode</name>
<value><int>405</int></value>
</member>
<member>
<name>faultString</name>
<value><string>本站点禁用XML-RPC服务。</string></value>
</member>
</struct>
</value>
</fault>
</methodResponse>其实博主试了下用正确的账号密码获取的提示也是错的?????不知道是WP修复了,还是哪里博主已经配置了。目前现象就剩下服务器CPU爆满,该如何让阿祖收手呢?得告诉他里面都是肥龙,但我也不知道在哪=^=
想了想,最后直接在入口nginx上直接拦截,这样就不会进入到php-fpm了,顺便造一个错误响应,嘻嘻嘻嘻。。。。
<?xml version="1.0" encoding="UTF-8"?>
<methodResponse>
<fault>
<value>
<struct>
<member>
<name>faultCode</name>
<value><int>405</int></value>
</member>
<member>
<name>faultString</name>
<value><string>Er right right right,think too much.</string></value>
</member>
</struct>
</value>
</fault>
</methodResponse>所以最后nginx server增加location块处理该请求
location ~* /xmlrpc.php {
#default_type application/json;
default_type text/xml;
add_header Access-Control-Allow-Credentials true;
add_header Access-Control-Allow-Origin *;
add_header Cache-Control public;
add_header Cache-Control max-age=300;
return 405 '<?xml version="1.0" encoding="UTF-8"?>\n<methodResponse>\n <fault>\n <value>\n <struct>\n <member>\n <name>faultCode</name>\n <value><int>405</int></value>\n </member>\n <member>\n <name>faultString</name>\n <value><string>Er right right right,think too much.</string></value>\n </member>\n </struct>\n </value>\n </fault>\n</methodResponse>\n';
}
正文完

 隐私政策
隐私政策 留言板
留言板 金色传说
金色传说 kubernetes
kubernetes terraform
terraform 云生原
云生原 helm
helm 代码编程
代码编程 Java
Java Python
Python Shell
Shell DevOps
DevOps Ansible
Ansible Gitlab
Gitlab Jenkins
Jenkins 运维
运维 老司机
老司机 Linux 杂锦
Linux 杂锦 Nginx
Nginx 数据库
数据库 elasticsearch
elasticsearch 监控
监控 上帝视角
上帝视角 DJI FPV
DJI FPV DJI mini 3 pro
DJI mini 3 pro 关于本站
关于本站